Bloomberg just made big news.
In its recent issue, it featured a cover story: “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies“, detailed how Chinese military planted malicious chips into motherboards manufactured by Taiwanese supplier, supplying motherboards to a major server provider whose servers were used by almost 30 US companies, including Amazon and Apple. And by doing this, Chinese military gains potential access to these companies and even US military.
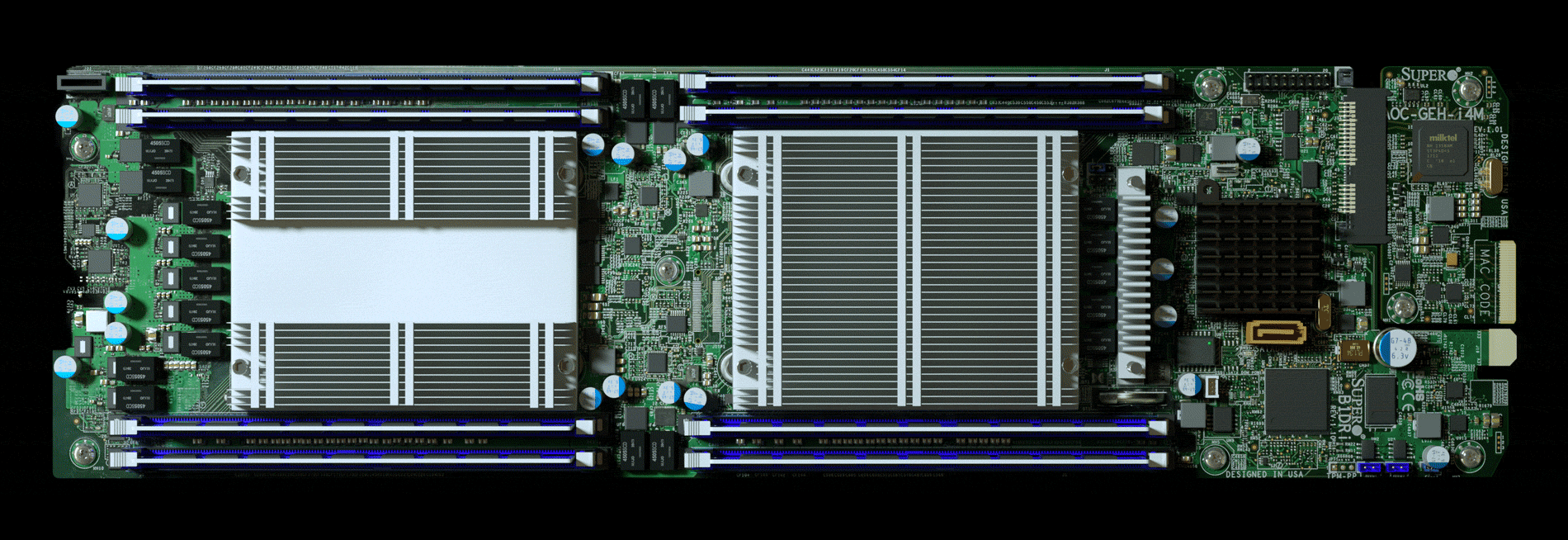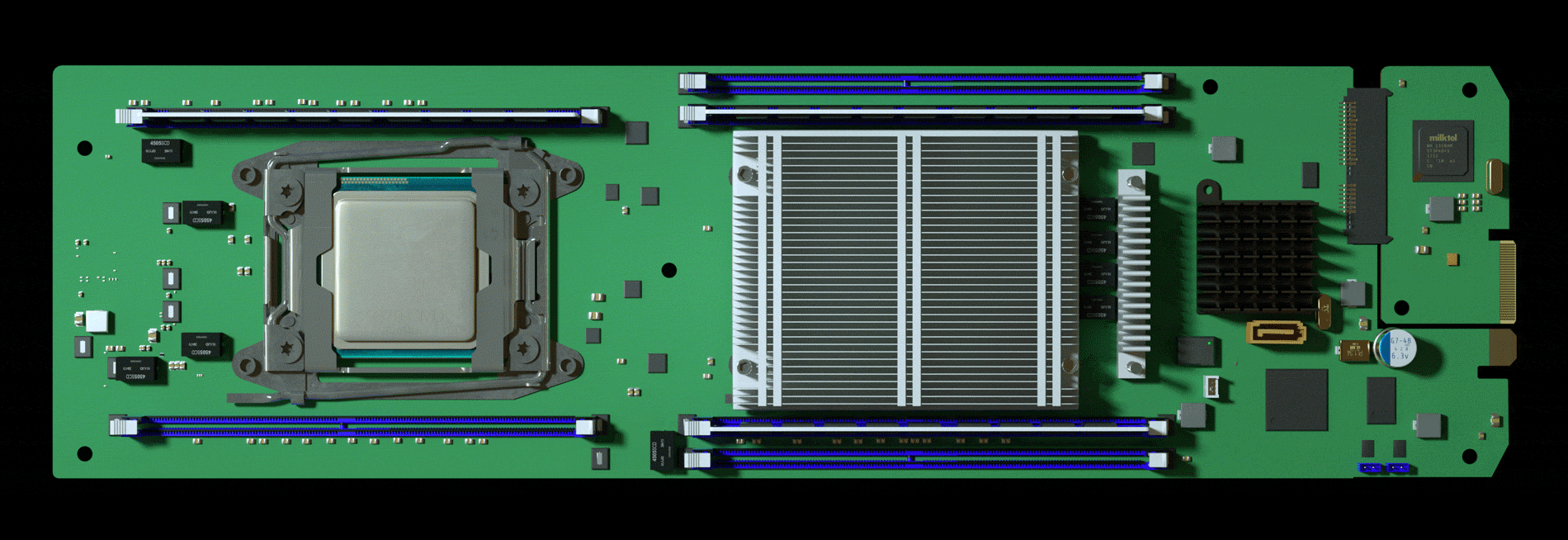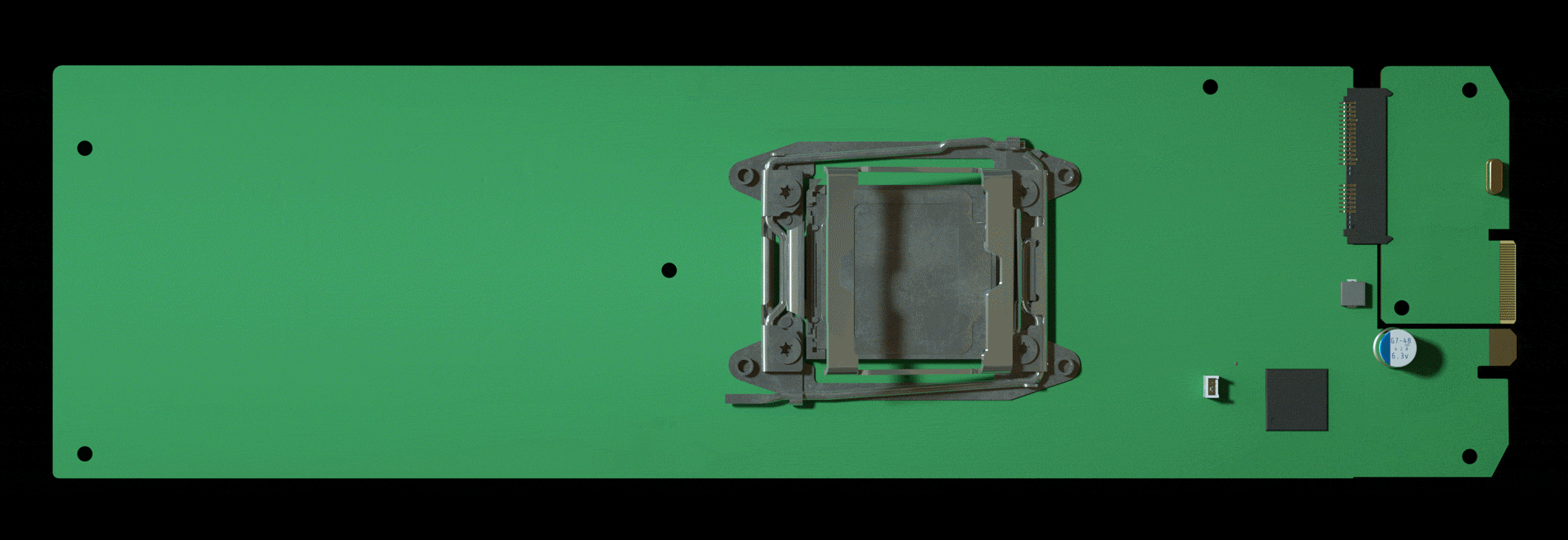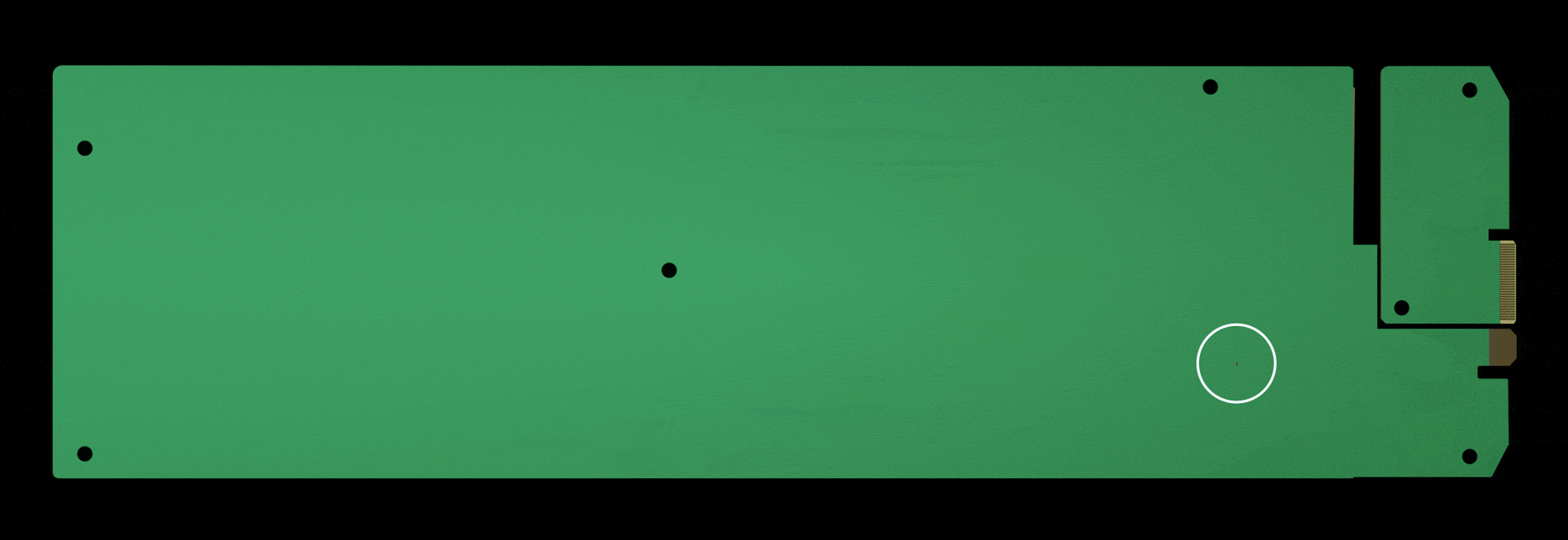
Here’s the malicious chip on the motherboard:
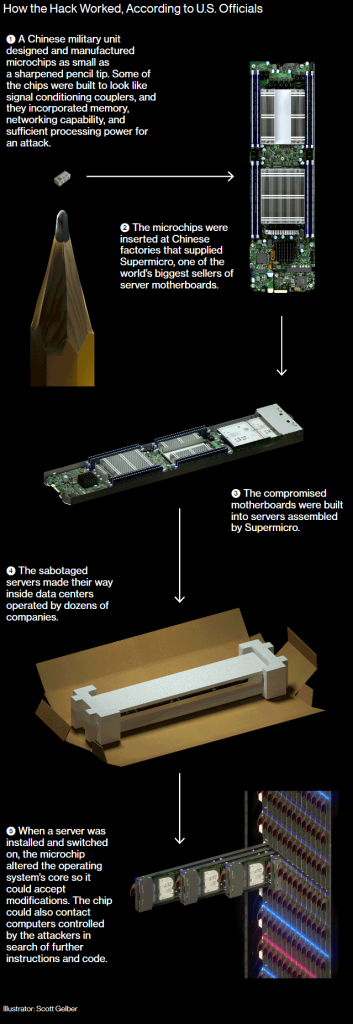
Here’s a illustration of that process directly from their website:
You don’t have to be a genius to know how big this is, in many ways.
Technically, this is very advanced. Just compare to what the NSA was found doing back in 2014:

I mean, what the NSA has done can be accomplished by just any organization with a team of security experts. What the Bloomberg described, needs collaboration of experts from different areas spanning different industries. It needs state level sponsorship. The only thing that comes comparable, is the Stuxnet.
But even Stuxnet pales in comparison in terms of long term impact. When Stuxnet was made public in 2010, it has already done its tasks. There were a lot of speculation before US and Israeli officials “half confirmed” its origin, but ultimately, its impact is largely limited to technology world.
The hack described in Bloomberg’s article on the other hand, will help re-shape the global supply chain in the years to come. It would be naive to think this is pure coincident that this hack was published almost the same time when Mike Pence spoke at the Hudson Institution.
Despite its length, the article actually doesn’t describe the hacking in detail. The chip in its cover photo (shown below) was dismissed by experts as a very cheap passive component, “not possible to do anything remotely related to hacking”.
The way the chip supposed to work is also vague. From the article, it seems the chip may hijack the code verification process to bypass some security check. But it is unclear whether it was the IPMI code verification or the UEFI code verification or both.
As of this writing, both Apple and Amazon have denied the claim the hack claim. However, the shell has been dropped and the storm is still brewing. Because despite all these refusals, it successfully made people believe that this kind of hack is possible, and it is only possible in mainland China. The seed has been planted. How lucky we are, to witness such historical drama unfolding before our eyes.